Recently, GBQ’s IT Services team shared thoughts on the cyber risk impact of the conflict in Ukraine. In a nutshell, we recommend that organizations keep an eye on the situation as most of the malicious cyber activity has been contained to the fighting theater (as each side tries to interfere with the other’s ability to wage war).
If your firm has an active cybersecurity program, we recommended you keep doing what you’ve been doing. However, we do believe accelerating testing and enhancing defenses is prudent.
If a firm does not have an active cybersecurity program, we recommend developing one now. There is no time like the present to start acting on cybersecurity.
Together with the FBI and numerous authorities in the cybersecurity realm, our team agrees that, at some point, this conflict is going to spill out into cyberspace and impact the US directly. As an update to our article, we’ve abstracted information from Info Tech Research Group, an information technology research and advisory company that the GBQ IT Services team utilizes to empower growth of our clients. Info Tech recently provided details on the following topics:
- Cyberattacks to Watch For
- Notable Advanced Persistent Threats (APTs) and Groups to Track
- Recommendations for Immediate Action
- Additional Resources to Monitor the Situation
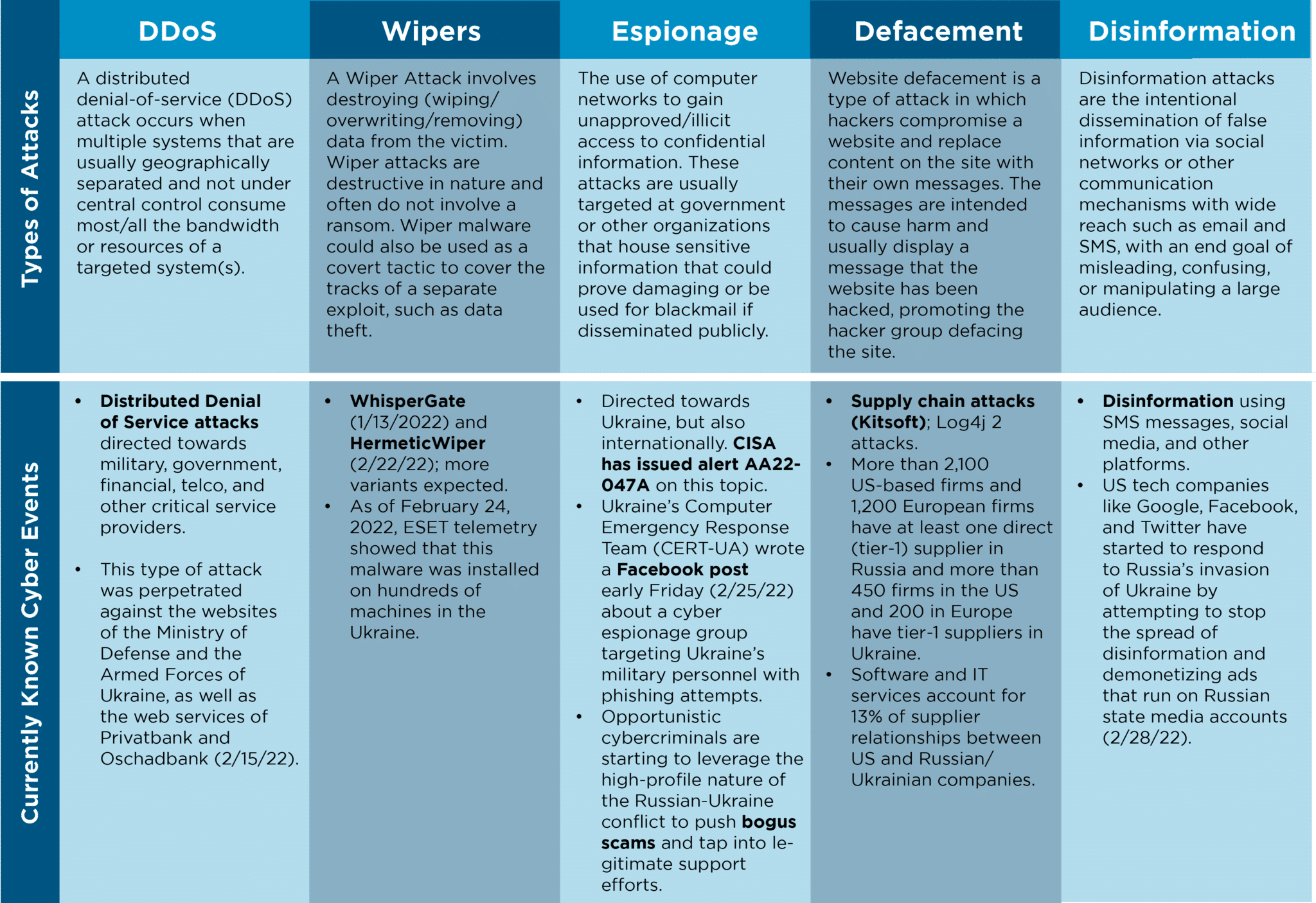
Cyberattacks to Watch For
Cyberattacks come in various “flavors” and the following table shows attacks experienced so far. IT teams should be working to understand the attacks as well as the safeguards that must be in place to fend them off. It is key to know how effective your defenses are against these types of attacks.
Notable Advanced Persistent Threats (APTs) and Groups to Track
An advanced persistent threat is a stealthy threat actor, typically a nation-state or state-sponsored group, which gains unauthorized access to a computer network and remains undetected for an extended period of time. IT teams should stay informed and vigilant concerning the threat actors currently associated with Russian attributed cyberattacks. Many of these attacks fit the APT model meaning they could be resident in a system now but dormant. These threat actors are already perpetrating attacks against Ukraine. Companies should understand the attacks being used and build appropriate defensive measures, in case they shift their attention to the rest of the world.
The CISA Shields Up site, SANS Storm Center site and MITRE ATT&CK group site are helpful for receiving timely information and understanding risks.

Recommendations for Immediate Action
Info Tech makes the following recommendations for firms that have an active cybersecurity program or who have the technical acumen to look at these issues.
1. Improve network monitoring at your perimeter. Ensure you have visibility for incoming and outgoing traffic with appropriate safeguards.
-
- Monitor and consider blocking high-risk outbound network traffic:
- SSH (TCP 22)
- MSRPC (TCP 135)
- SMB (TCP 139, 445)
- Unsecured LDAP (TCP 389)
- Secured LDAP (TCP 636)
- MSSQL (TCP 1433)
- RDP (TCP/UDP 3389)
- WinRM (TCP 5985, 5986)
- Review your Web Application Firewall (WAF) configuration and set it to blocking mode to mitigate zero-day attacks.
- Log, correlate and review events. Focus on threat intelligence, lower alerting thresholds if possible, and be aware of risk patterns associated with Russian actor tactics, techniques, and procedures (TTPs).
- Monitor and consider blocking high-risk outbound network traffic:
2. Create contingency plans to disconnect high-risk external connections:
-
- Inventory any unfiltered VPNs and other vendor/contractor connections. Make sure you have monitoring in place and understand access risks.
- Limit traffic destinations for high-risk protocols wherever possible.
- Watch for collateral damage and propagation via automation. NotPetya showed us that poorly monitored and unpatched interconnected systems provide reliable attack surfaces.
- Perform tabletop exercises to ensure readiness during any disruptive event and at least annually. Ensure all your key resources have current contact information and can support business continuity on short notice.
- Validate your backup and recovery processes.
3. Use this event to bolster your security awareness program. Educating end-users will lower your risk from malware and social attack vectors as well as protect employees at home.
-
- Implement or execute a simulated phishing campaign. These attacks are usually carried out via email but now are frequently delivered via SMS, phone calls, and social media. Ensure your employees are vigilant.
- Reassess your password standard. Encourage passphrases and strong passwords: easy to remember, hard to guess. Use a secure password manager to reduce call center events due to users who use complex, hard-to-guess passwords.
- Implement Multi-Factor Authentication (MFA) on any external ingress points. Consider expanding the scope to those that don’t store or transmit sensitive information. If they pose a risk by being able to pivot to other systems if compromised, assume the worst.
- Timely and effective communication is paramount. Consider the human factor: most people are scared during conflicts. You’ll receive the best outcome by keeping your communications simple, actionable, and direct while delivering with calmness.
4. Improve your rigor around patching and update consistently. Poorly monitored, unpatched assets create additional risk.
-
- Ensure your assets are patched and up to date (computer systems, mobile devices, applications, etc.). Automatic updates are strongly encouraged.
- Ensure your endpoint detection and response agents are active, receiving threat intelligence feeds, and set to protect/block risks.
- Enable an allow-listing policy on your EDR solution (which files can execute). Recent attacks have shown that Russian actors have misused legitimate drivers from trusted vendors, such as EaseUS (Partition Master), to weaponize wiper attacks and in some cases bypass poorly configured or mismanaged EDR/MDR.
- Look for behavioral evidence or network and host-based artifacts from known Russian state-sponsored TTPs. Table 1 from CISA’s Alert (AA22-011A) lists commonly observed TTPs.
If your firm does not have a formal cybersecurity risk program, consider making the investment to put one in place.
Additional Resources
CISA Shields Up provides the latest cyber risk updates on the Russia-Ukraine conflict and should provide the most value for staying informed.
Misinformation is also a major attack vector for malicious actors. In fact, sophisticated disinformation campaigns are a part of the cyber warfare occurring in the conflict.
Follow only reliable sources for cyber alerts and actionable intelligence.
| Informational Resources | URL |
| CISA (US Cybersecurity & Infrastructure Security Agency) | https://www.cisa.gov/uscert/ncas/alerts |
| CISA Known Exploited Vulnerabilities Catalog | https://www.cisa.gov/known-exploited-vulnerabilities-catalog |
| SANS Internet Storm Center | https://isc.sans.edu/ |
| CISA Shields Up | https://www.cisa.gov/shields-up |
| Computer Emergency Response Team of Ukraine | https://cert.gov.ua/articles (in Ukrainian) |
| Understanding and Mitigating Russian State-Sponsored Cyber Threats to U.S. Critical Infrastructure |
https://www.cisa.gov/uscert/ncas/alerts/aa22-011a |
GBQ IT Services
GBQ IT Services is a team of technology and business professionals – builders, breakers, analysts, operators, and auditors with broad and deep experience across our service offerings. You can count on our dedication when serving up the solutions your business needs:
- Plot Strategy
- Reduce Risk
- Build and Measure Productivity
- Assure Stakeholders
To discuss this information in more detail, contact our IT Services team today.
