Cyberattacks are inevitable. Are you prepared?
It’s not a matter of if, but when. As the digital landscape evolves, businesses face increasingly complex challenges and costly concerns in remaining secure. That’s why industry leaders count on GBQ to provide unique and tailored solutions to safeguard their most valuable assets, including data, networks, systems, and personnel, while maintaining trust with key stakeholders. Who is equipping you with a sophisticated and comprehensive cybersecurity plan to empower growth?
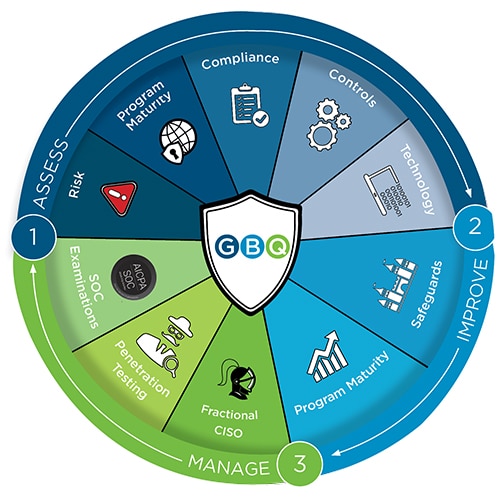
Rely on GBQ’s cybersecurity team to:
- Assess and illustrate your company’s unique cyber risk posture and capabilities to create a comprehensive cybersecurity plan that invests in preventing and managing cyber risks.
- Improve your company’s risk posture, providing a competitive advantage in the industry by demonstrating a commitment to a risk-aware culture and resilience.
- Manage a resilient program to sustain regulatory compliance requirements against evolving cyber threats and digital risks.