The 2024 Verizon Data Breach Investigations Report (Verizon DBIR) noted system intrusion and miscellaneous errors as two of the top three attack vectors for threat actors. To thwart these two attack vectors, organizations must develop and implement a strong vulnerability management program.
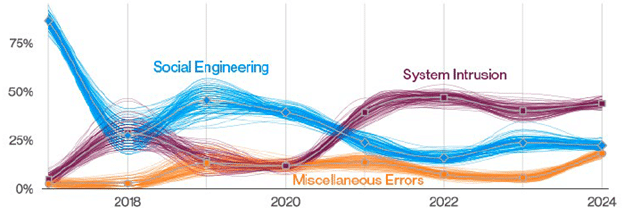
Figure 1: Verizon DBIR Top patterns over time in Manufacturing Industry breaches
Managing vulnerabilities is a crucial component of cybersecurity, yet it frequently suffers from poor design or misalignment with an organization’s business objectives. Essentially, a vulnerability management program aims to detect, manage, prioritize, and mitigate security vulnerabilities throughout an enterprise’s IT ecosystem.
A vulnerability management program can be broken into five main steps: asset management, configuration management, patch management, compensating controls, and validation.
Asset Management
Being the first control in the Center for Internet Security’s Critical Security Controls (CIS CSC v8) and featured across various control families within the Payment Card Industry Data Security Standard (PCI-DSS v4.0), asset management is critical. One cannot secure what one is unaware of. Establishing robust asset management and discovery processes is fundamental, and possibly the most crucial stage, in a vulnerability management program.
Configuration Management
Vulnerabilities can stem from multiple sources, such as exploiting third-party software vulnerabilities externally or through inadequate device configurations internally. Configuration mistakes are a significant source of self-imposed risks within an organization. Adopting secure baselines, in line with CIS benchmarks or similar standards and ensuring strong change management practices, is essential for protection against various errors. Furthermore, misconfigurations in Active Directory could give attackers opportunities to elevate their access rights, allowing them to conduct more severe attacks on network resources.
Patch Management
Patch management is essential, with automation as a key to maintain systems in the current technological landscape. While smaller organizations might use Windows Automatic Update for patches, it’s important to note that this service only covers operating system updates. Using a tool such as Qualys can help automate patching of both windows and select third party software.
Compensating Controls
Sometimes, patching is not an option. A device may be too old to support the latest patch, or a patch may break some critical functionality. In these cases, compensating controls can be used to mitigate the risk of exploitation. Compensating controls are alternative security measures that provide equivalent or comparable protection to the original control. For example, if a device cannot be patched, it can be isolated from the network, protected by a firewall, or monitored by an intrusion detection system.
Validation
The final step of a vulnerability management program is validation. Validation is verifying that the previous steps have been implemented correctly and effectively. Validation is completed through vulnerability scanning, internal or third-party audits, and penetration tests. The goal of validation is to ensure that the organization’s security posture is aligned with its risk appetite and compliance requirements.
Contact GBQ’s IT Services team to discover the ways we can assist with the creation and implementation of your vulnerability management program and ongoing validation efforts through regular risk assessments, vulnerability assessments and penetration tests.
Article written by:
John Stuart
Manager, GRC and Cybersecurity
