The SOC for Cybersecurity report demonstrates an organization’s cybersecurity risk management efforts. It is appropriate for companies who want to provide assurance that the appropriate tools, processes, and controls are in place to manage a cyber-attack. This report can be distributed to an organization’s senior management, Board, analysts and investors, and business partners.
Unlike the SOC for Service Organizations reports (SOC 1, SOC 2, SOC 3), the SOC for Cybersecurity report is not focused solely on service organizations; any enterprise can choose to have a SOC for Cybersecurity examination performed.
The control criteria covered by a SOC for Cybersecurity report is flexible and can be any suitable framework meeting certain criteria, such as:
- SOC 2 Trust Services Criteria for Security, Availability and Confidentiality
- NIST Cybersecurity Framework
- ISO 27001
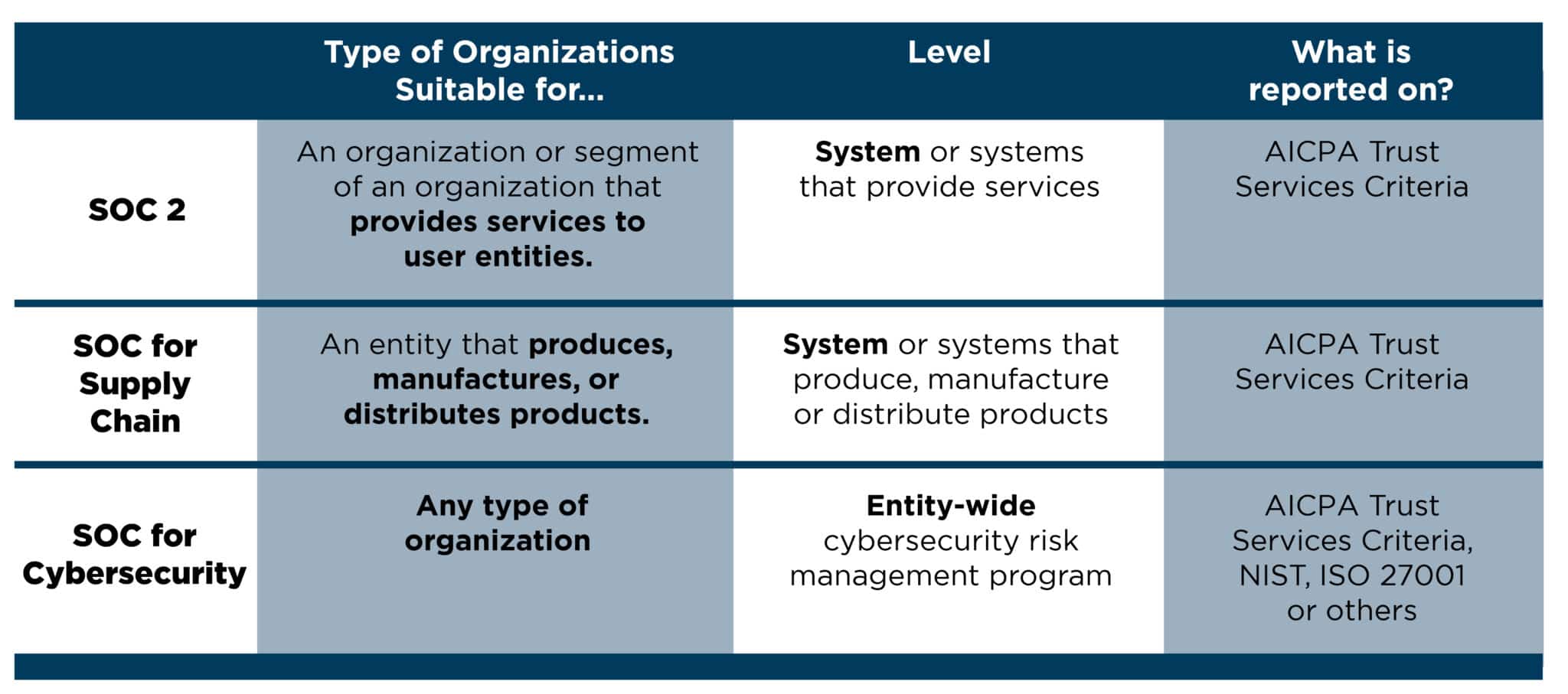
What is the difference between SOC 2, SOC for Supply Chain and SOC for Cybersecurity?
Benefits of SOC for Cybersecurity:
- Independent Validation of Your Cybersecurity Diligence: Customers, partners, investors, and internal stakeholders don’t simply have to take your word for it.
- Competitive Advantage: As SOC for Cybersecurity is a relatively new examination, few competitors will be capable of producing a report affirming their cybersecurity practices. These reports are for general use, so you can distribute them at your discretion without restrictions.
- Enhanced Position Against Data Breaches: With a SOC for Cybersecurity report, you reassure external stakeholders of your organization’s sound practices while proactively educating and enhancing internal processes before potential issues arise.